Deobfuscating Cisco Type 7 Passwords
Overview
What is a Cisco Type 7 password?
Cisco Type 7 passwords are obfuscated passwords used in Cisco devices to protect sensitive information, such as login credentials. These passwords are not encrypted but rather encoded/obfuscated using a simple XOR operation. This encoding is reversible, allowing you to deobfuscate the password and reveal the original plaintext value.
Gaining access to the switch’s file system and configuration file
-
Connect to the switch using a console cable.
-
Interupt the boot process of the switch by powercycling the switch and hold the “mode” button.

You will be dropped into the switch’s bootloader prompt:
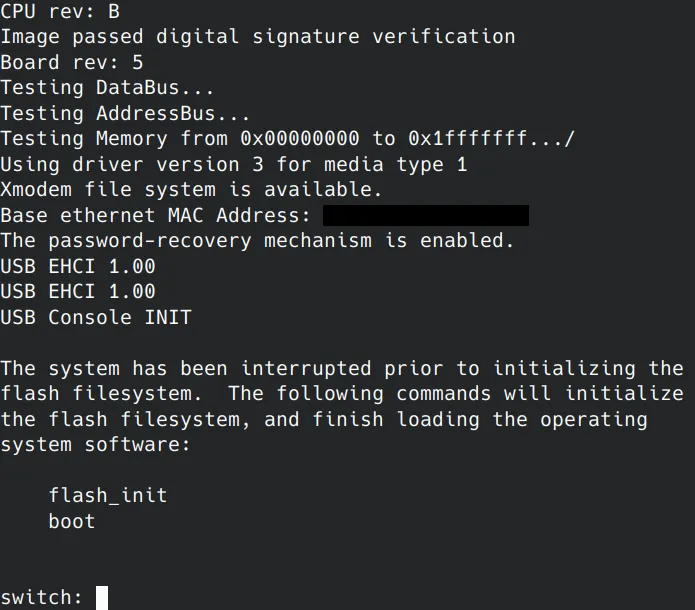
-
Initalize the switch’s flash file system by running the following command:
Terminal window flash_init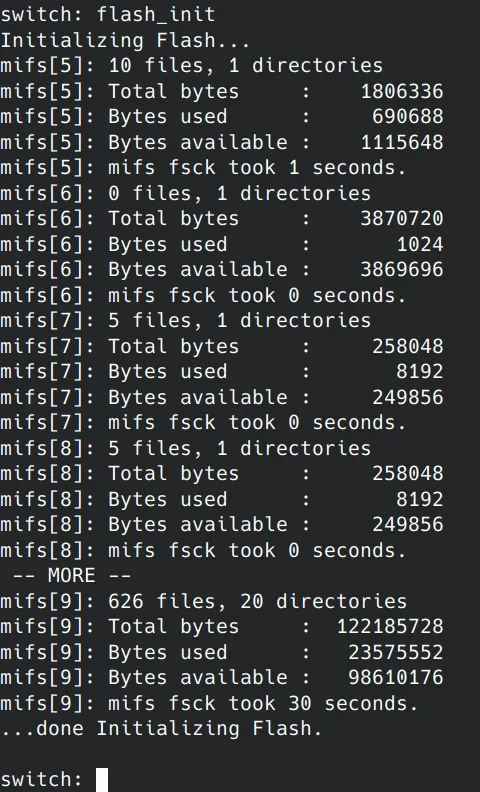
-
List the contents of the flash file system to identify the configuration file:
Terminal window dir flash: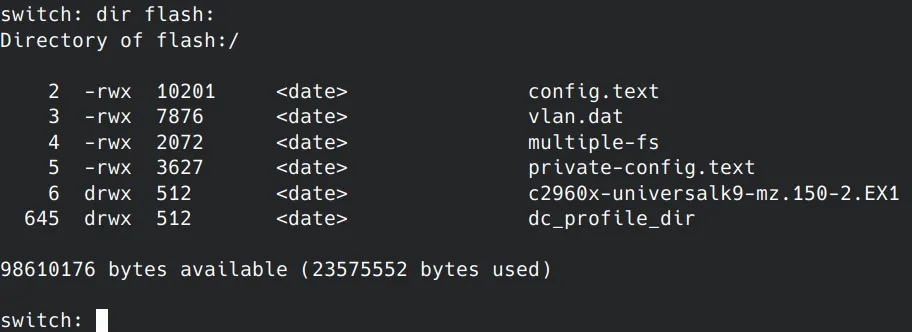
-
Concatinate the configuration file to the console output:
Terminal window cat flash:/config.text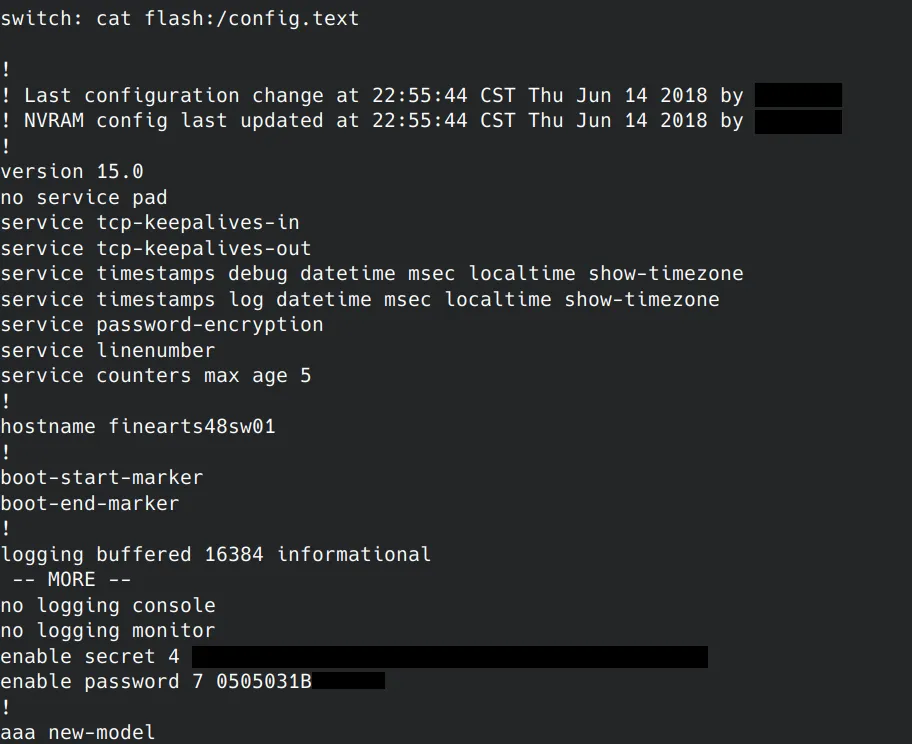
Type 7 Password Deobfuscation
After you have obtained the configuration file, you can use the following Python script to deobfuscate the Type 7 passwords, or you can use the web based tool below.
#!/usr/bin/env python3
"""Based on the documentation from:- http://pen-testing.sans.org/resources/papers/gcih/cisco-ios-type-7-password-vulnerability-100566- http://wiki.nil.com/Deobfuscating_Cisco_IOS_Passwords
translation = [ 0x64, 0x73, 0x66, 0x64, 0x3b, 0x6b, 0x66, 0x6f, 0x41, 0x2c, 0x2e, 0x69, 0x79, 0x65, 0x77, 0x72, 0x6b, 0x6c, 0x64, 0x4a, 0x4b, 0x44, 0x48, 0x53, 0x55, 0x42, 0x73, 0x67, 0x76, 0x63, 0x61, 0x36, 0x39, 0x38, 0x33, 0x34, 0x6e, 0x63, 0x78, 0x76, 0x39, 0x38, 0x37, 0x33, 0x32, 0x35, 0x34, 0x6b, 0x3b, 0x66, 0x67, 0x38, 0x37]"""
import argparse
translation = [ hex(ord(char)) for char in 'dsfd;kfoA,.iyewrkldJKDHSUBsgvca69834ncxv9873254k;fg87']
def hexadecimal(text): return int(text, 16)
def decrypt(text): password = '' jump, text = int(text[:2]), text[2:] for i in range(0, len(text), 2): password += chr(hexadecimal(text[i:i+2]) ^ hexadecimal(translation[jump])) jump += 1 % len(translation) return password
def argument_parser(): parser = argparse.ArgumentParser(description='A simple utility to decrypt cisco Type 7 passwords') parser.add_argument('text', nargs='+', help='the encrypted password that you want to decrypt') parser.add_argument('-l', '--long-output', action='store_true', help='show a message with the encrypted and decrypted password') return parser
def main(): args = argument_parser().parse_args() for text in args.text: if args.long_output: print('{}::{}'.format(text, decrypt(text))) else: print(decrypt(text))
if __name__ == '__main__': main()Source: Eduardo-Ortega102/cisco7decrypt.py
This Python script does not have any external dependencies.
Script Usage
Ensure you have the script marked as executable:
chmod +x cisco7decrypt.pyRun the script with the encrypted password as an argument:
./cisco7decrypt.py <encrypted_password>Example:
$ ./cisco7decrypt.py 121A0C041104ciscoWeb Based Deobfuscation Tool
If you do not want to run the script locally, you can use the following web based tool to deobfuscate the Type 7 passwords:
Cisco Type 7 Password Deobfuscator
Enter a Cisco Type 7 obfuscated password to reveal the plaintext. Type 7 passwords typically start with two digits followed by hexadecimal characters.
Warning: This tool is for educational purposes only. Always ensure you have proper authorization before attempting to deobfuscate passwords.
Note: This tool processes passwords locally, there is no data within this form that is transmitted to any server.